HITRUST’s comprehensive set of tools, resources, and products provide an integrated approach to aligning, maintaining, and supporting information risk management and compliance at an organizational level.
What HITRUST CSF Certification Means for an Organization
Most organizations today have a firmer handle on cybersecurity measures to mitigate risk and protect their data, but the reality is that the cyber landscape is constantly changing. Enter the HITRUST Common Security Framework (CSF) Certification.
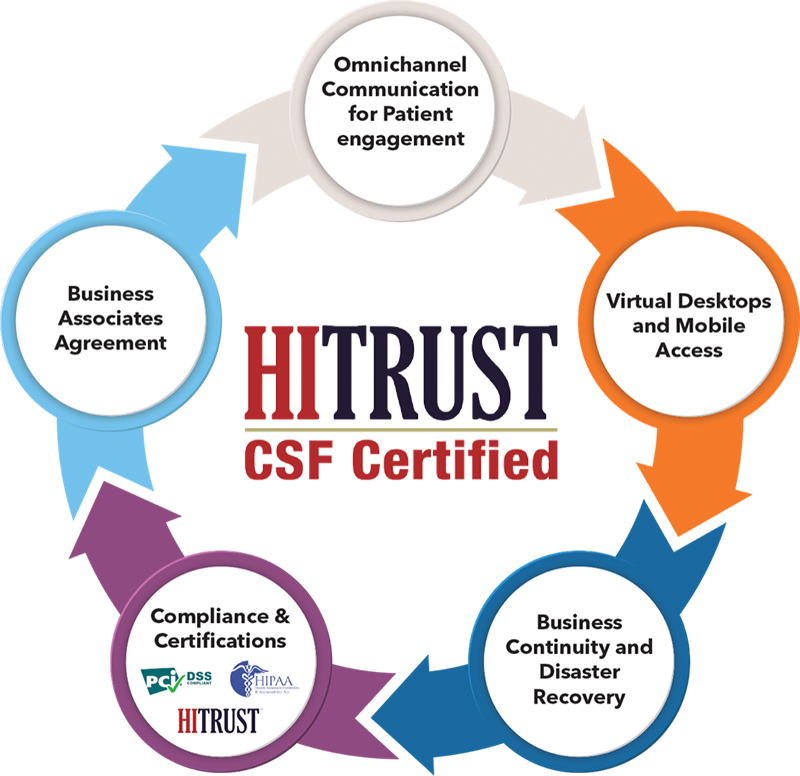
HITRUST CSF is globally recognized and demonstrates that an organization is adhering to the highest information security standards. Gaining certification shows that an organization is proactive in its approach to data protection and risk mitigation. Becoming HITRUST certified is no walk in the park, as organizations will need to be externally assessed by a third party, and the process can be both costly and time consuming. HITRUST’s quality assurance team will perform QA on this third-party assessment for quality and consistency.
That said, certification can be used to reassure partners that they are compliant and up-to-date with industry-specific regulations, such as HIPAA, NIST, PCI, and over 40 other frameworks that an organization may be obligated to consider when choosing companies to work with.
The majority of US Healthcare providers view the HITRUST CSF control framework as extremely beneficial. 81% of hospitals and 83% of US Health plans utilize HITRUST CSF. In a 2018 survey by the Healthcare Information Management Systems Society (HIMSS), HITRUST CSF was the most widely adopted control framework in the healthcare industry.
MyCSF
No matter what industry your organization operates in, you know how challenging it can be to manage information security risks, data governance, comply with information protection regulations, and adhere to national or international standards.
HITRUST understands how overwhelming, resource-intensive, and complicated this can be for any organization. Using their dominant position in the industry and the experience gained over many years processing hundreds of thousands of risk assessments, they created MyCSF.
MyCSF is a Software as a Service (SaaS) solution that allows organizations to quickly and cost-effectively manage information risk and meet state, federal, and international privacy and security standards.
It allows businesses of all sizes to perform risk assessments and design corrective action plans. MyCSF also includes enhanced benchmarking and integration with GRC platforms and HITRUST Assessment XChange.
HITRUST Shared Responsibility Program
The HITRUST Shared Responsibility program looks at the challenges businesses face when dealing with their cloud service providers. The HITRUST Shared Responsibility Model (SRM) is the industry’s first commonly accepted model for sharing control responsibility in the cloud.
Organizations benefit from this model by ensuring that cloud service providers can communicate appropriate security and privacy assurances, get better guidance on the delineation of control ownership, and simplify customer assurance processes.
The shared responsibility matrix is designed to allow customers to discuss cloud-supply-chain risk. It has an out-of-the-box template pre-populated with shared responsibility for the cloud that includes over 2000 detailed security and privacy control requirements.
As a result, leading cloud service providers have partnered with HITRUST to jointly publish Shared Responsibility matrices. Cloud service providers HITRUST has partnered with include Amazon Web Services (AWS), Google Cloud, and MicrosoftⓇ Azure.
HITRUST Threat Catalogue
The Threat Catalog was designed over a multi-year period of time, in which HITRUST identified a complete set of threats, to help businesses improve their information security position.
Prior to the development of the Threat Catalogue, Dr. Bryan Cline explained, “…a comprehensive threat list that could support risk analysis and help organizations better understand and mitigate threats to sensitive information was essentially unavailable.”
The Catalogue maps the threats to controls in the HITRUST CSF Framework, allowing organizations to identify threats to sensitive information, assets, and operational threats.
Additionally, it also maps threats to less comprehensive threat lists from other frameworks, including the National Institute of Standards and Technology (NIST) and the European Union Agency for Cybersecurity (ENISA) Threat Taxonomy.
Learn more About HITRUST with our free ebook:

The HITRUST RightStart Program for Startups
From day one, startups have several unique challenges facing them, including the cost of addressing risk management and compliance. During the early years, this can put significant strain on a startup’s resources. HITRUST designed its RightStart Program to help new companies overcome the challenges of compliance and risk management.
To qualify for this initiative, a company must have:
- Been founded in the last three years
- A productive service line, or be close to having one
- Under 50 full-time employees
- Revenue under $10 million
HITRUST Venture Program
The HITRUST Venture Program was created specifically for high-potential startup companies, to help them accelerate innovation while integrating security, privacy, and compliance into their culture and strategy.
By leveraging the HITRUST Approach and HITRUST CSF certification, it reduces future potential risk, increases compliance, and is more attractive to potential customers while protecting their brand reputation.
The HITRUST Venture Program is open to companies who fulfill the following criteria:
- Founded or incorporated in the previous five years
- Have fewer than 100 full-time employees
- Are part of a VC firm that has joined the council
- Has annual revenue under $20 million